Scale AI with Your Existing Identity Stack
Runlayer extends your existing identity stack to give you the same control over MCP usage that you have over every other application in your organization, without slowing anyone down.
MCP Alone Breaks Your Identity Stack
Your teams are already connecting to thousands of external MCP servers to query databases, update tickets, and automate workflows. This is happening across every industry, completely outside identity and access systems.
AI connections skip Okta and Entra entirely. No SAML, no OIDC, no authentication policies.
No conditional access on AI tools. No device compliance, no location-based restrictions, no role-based provisioning.
No visibility into who's accessing what AI tools and data. Can't track provisioning, can't audit usage, can't enforce offboarding.
AI that works the way your stack already does
MCP is automating workflows that used to take hours or days. Runlayer makes MCP work like enterprise apps: same identity providers, same access policies, same deployment model. Enable AI transformation without rebuilding your IAM stack.

Native Okta and Entra integration: SSO, SCIM provisioning, and conditional access apply to MCP the same way they apply to Slack or GitHub.
Enforce context-aware policies on MCP: scope access by user, device, location, and session without building new auth systems.
Manage MCP access in the same dashboard you use for everything else. Provision, audit, and offboard from one place.


"Every AI tool is rushing to add MCP capabilities, but there's no way to manage the chaos across them all. We needed a centralized control plane as MCP sprawl became a real concern at Gusto. Runlayer is solving this - they're building the golden path for using MCPs in a secure, enterprise-ready manner."
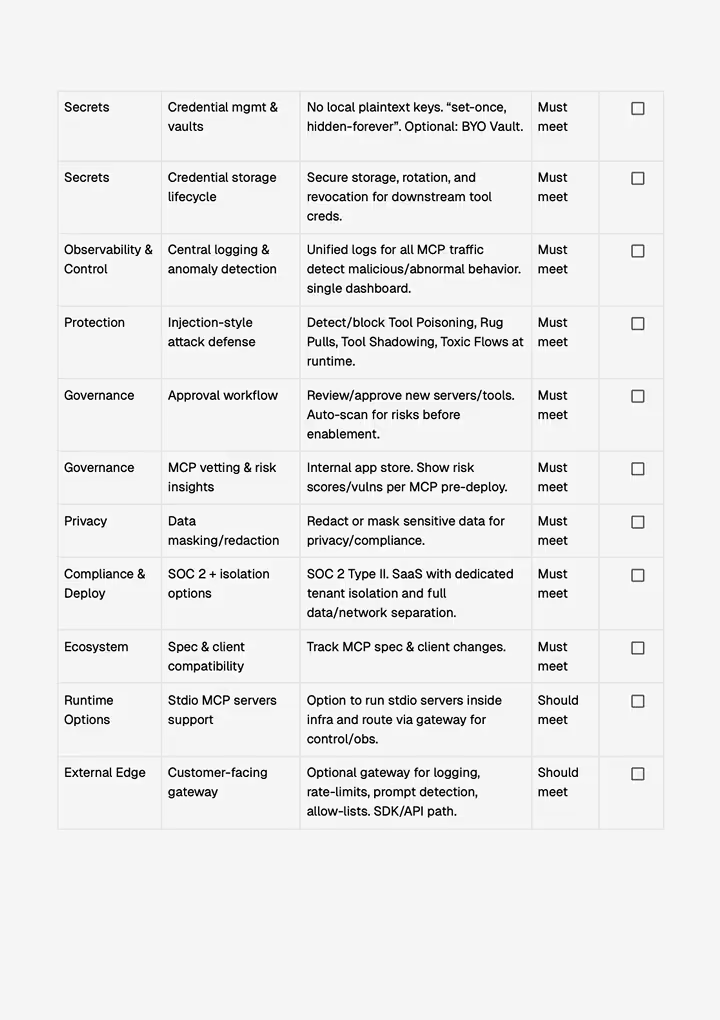
Covers threat detection, access control, audit requirements, and compliance frameworks.
Deploy Once.
Manage Everywhere.
Enterprise-grade infrastructure that integrates with your existing stack. Works with your current AI tools and identity systems. Self-hosted deployment in 10 minutes with the same governance patterns you use for other enterprise software.

SSO, SCIM provisioning, and conditional access policies apply to MCP the same way they apply to Slack or GitHub. Automatic user/group sync with MCP access tied to your org chart.
Self-hosted behind your VPC or multi-tenant SaaS. Deploy via Terraform (ECS) or Helm (EKS) in 10 minutes. No agents, no proxies, no data egress. Low-latency security scans because the gateway runs in your cloud.
IT controls the catalog. Developers get one-click install. Every MCP server is vetted and scored before it reaches your organization. Support for 18,000+ external servers plus your internal tools. Version control and rollback built in.
Context-aware authorization based on user, device, client, server, session, and request attributes. Fine-grained permissions per tool and resource. Scope bloated APIs like GitHub's 106 tools down to 4 safe ones. Device-based restrictions via MDM integration.
Complete visibility into MCP usage across all teams and clients. Track tool calls, user activity, security violations, and adoption metrics. Export to Datadog, Honeycomb, or your logging stack via OpenTelemetry.
Provision MCP access automatically based on Okta groups, departments, or roles. Onboard new employees with the right tools on day one. Offboard instantly when someone leaves.
Built to Enable AI for Every Team
Enable AI Adoption with Visibility and Control

Build 3.4x faster.
Never leave your IDE again.


Discover How To Map Runlayer to Your Stack
Tell us your existing identity stack and we'll walk through deployment best practices, integration timelines, and how our enterprise customers went from pilot to production in weeks.

Frequently Asked Questions
All 300+ MCP clients including Cursor, VS Code, Claude Code, GitHub Copilot, ChatGPT, Claude Desktop, Windsurf, and any client that implements MCP.
No, we work with your existing IDE and AI client with the only difference being authentication through company SSO instead of personal API keys.
Request through the catalog: security-approved servers are available immediately with one click, while new servers go through fast-tracked approval in minutes instead of weeks.
Yes, with zero installation friction and the same governance/observability as remote servers, plus CLI tools to make local-to-hosted workflows seamless.
We integrate with Okta and Entra for identity, enforce the same conditional access and device compliance checks you use everywhere else, and provide complete audit trails, so AI becomes like another enterprise application, not a special case.
No, scans run with low latency and you get one-click access instead of manually configuring JSON files.
Yes, your development experience stays identical. you just get access to vetted, secure MCP servers instead of random GitHub repos.
Yes, we help convert internal APIs into MCP servers that appear in the catalog alongside external ones with identical access controls and observability.
Minimal disruption: we import existing configurations and your prompts/workflows remain the same, with most teams starting new servers through Runlayer then gradually migrating existing ones.