Cursor Hooks + MCP Security: Official Runlayer Partnership Announcement
We’re excited to be a launch partner for the new Cursor Hooks product. Cursor Hooks allow Cursor users to observe, control, and extend agents with custom scripts. With the integration between Cursor Hooks and Runlayer, security teams get visibility and control over MCP usage across their organization, all without disrupting how developers work.
MCP adoption is outpacing security
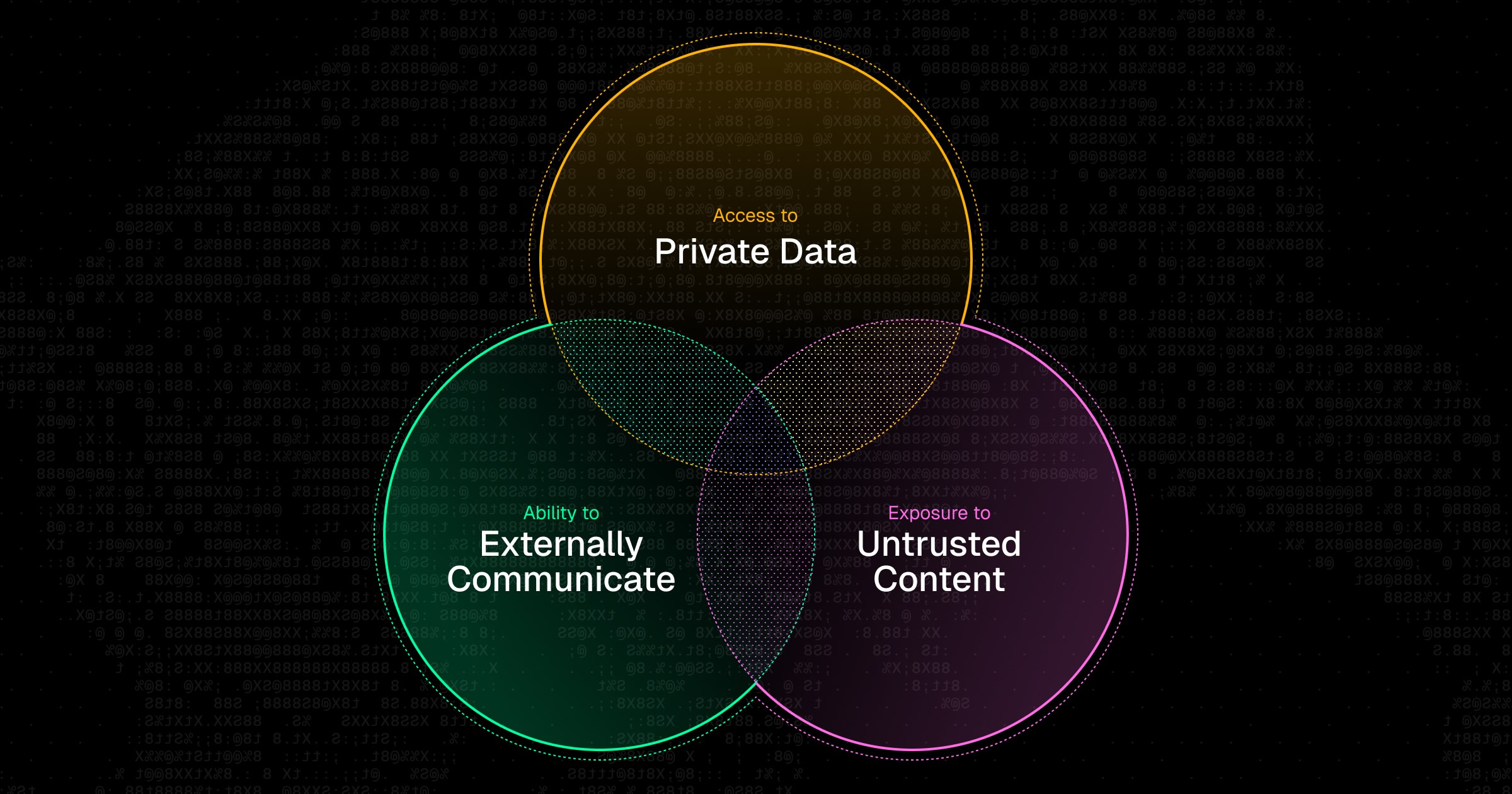
Developers are connecting AI agents to everything: GitHub, Slack, Notion, databases, internal APIs, etc. MCP makes this trivially easy, and there are now over 18,000 servers to choose from.
Which servers are your developers using? What data flows through them? Is that random MCP server someone found on GitHub actually safe? Most security teams don't have answers to these questions. They often don't know what questions to ask.
What Cursor Hooks changes
Cursor Hooks blocks any MCP server that isn't managed by Runlayer.
.png)
The only servers that run are the ones that have already gone through Runlayer's security scanning and your approval workflow. Side-loading random MCPs from GitHub is disallowed.
Shadow MCP detection and real-time security scans
Runlayer identifies shadow MCP usage and surfaces it before it becomes a problem. Every MCP server that passes through Runlayer is scanned in real time for security risks.
When someone tries to use an unauthorized MCP server, they're met with a denial:
Meanwhile, when they use an approved one: nothing. It just works. Both events show up in your audit logs.
To provide end-to-end observability, Runlayer documents all access grants or denials in Runlayer Audit Logs.
Setup takes five minutes
You can access an installation script in your Security Scanners page.
- Copy one command from your Runlayer workspace
- Push it through your MDM
- That's it!
If you're using an MDM solution like Rippling, Jamf, Intune, or Kandji, you can include this in your device installation scripts so all employee machines are protected by Runlayer.
Once deployed, every machine in your fleet enforces the same policies. Developers don't install anything. They don't change how they work. The security layer is invisible until it blocks something it should.
Why this matters
MCP is becoming standard infrastructure. Every AI tool is adding support: Cursor, Claude, VS Code, GitHub Copilot. Your developers will use it whether you have a strategy for it or not.
Cursor Hooks + Runlayer gives you a way to get ahead of that. One MDM deployment, company-wide enforcement, complete audit trail. No chasing individual developers or hoping they follow best practices.
.jpg)